
STAYSAFEONLINE
WITH
WEBHAWK
(CyberThreatSecurity)

BASES
COVERED

AttacksPreventedbyWebhawk
Denial of
Service attack
Sync Flood
Attack
DNS Spoofing
DNS Flood
Attack
DRDOS Attack
DNS cache
Poisoning
Session
Hijacking
Man-in-the-
Middle Attack
Backdoor
attacks
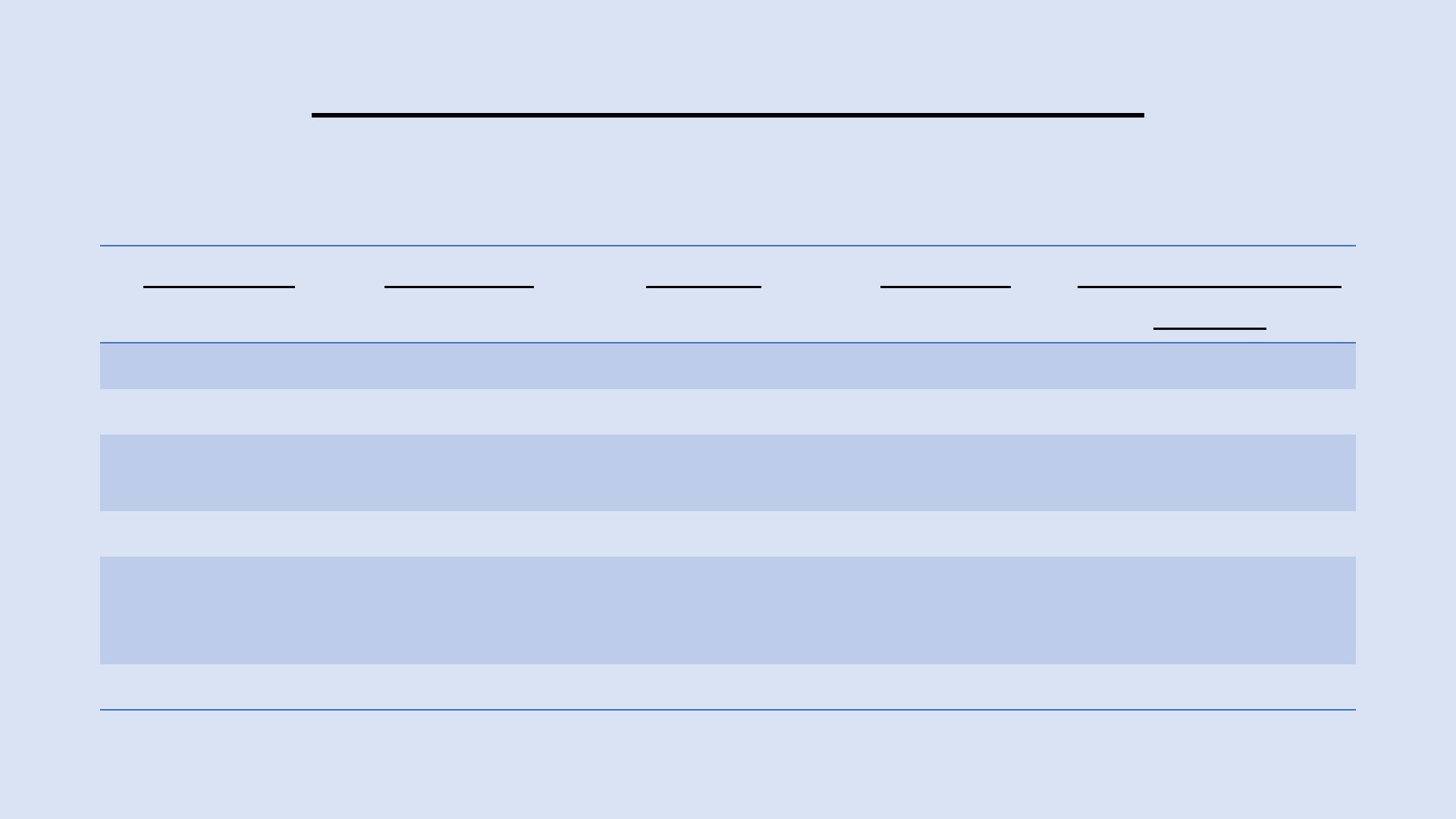
ComparisontoOtherSolutions
Protection WebHawk Firewall Antivirus Standard Wireless
Routers
Hacks Y N N N
Malware Y LIMITED N N
RuleBased
Protection
Y Y Y N
BehaviorLearning Y N N N
Securesall
connecteddevices
(notjustPCs)
Y Y N N
AutomaticUpdates Y N N N